Secure XML Traffic Between Storefront and Delivery Controller (DDC) IMP
Website Visitors:If you’d like to secure xml traffic from storefront to DDC, you should install certificates on the DDC. If you have IIS installed in your DDC server, then mapping the certificate to 443 is very straight forward process. Open IIS manager (inetmgr), select your server and then select server certificates. Import the certificate along with private key and bind it to 443. If you do not have IIS installed in your DDC server, then you should install the certificate on the DDC server and run netsh commands to link that certificate to citrix DDC software. Run below commands on powershell console.
|
|
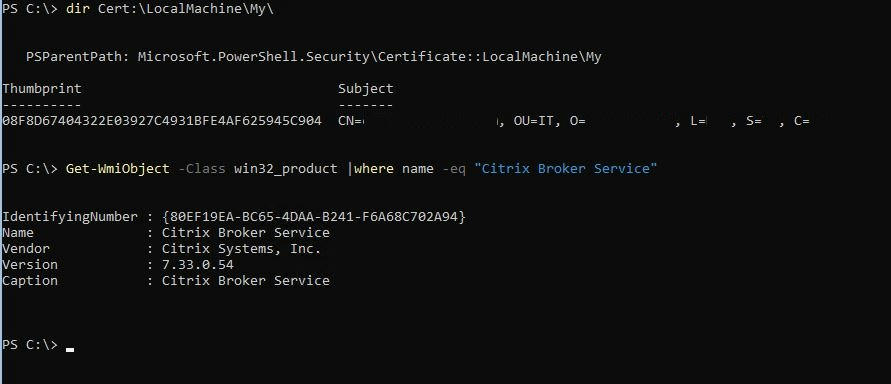
Commands displaying thumbprint of certificate and broker service
Now you need to map the certificate thumbprint to Citrix Broker Service. Run the below command on elevated command prompt or powershell console to do so.
|
|
Here, in the place of 0.0.0.0, you can also add the ip address of your DDC server. If everything is good, you should see “SSL certificate successfully added” message on your screen.
Where ever you have used DDC url like, SF or NetScaler, change the path to https like, https://ddc1.company.com. Also, open https://ddc1.company.com url in your browser. As the certificate mapping is complete, you should not see any cert errors in your browser. If you have IIS installed, you will see a default page if IIS is installed. If not, you will see a page not found error but no certificate error.
Troubleshooting
When all the above steps are followed, you might end up in “The parameter is incorrect” error as shown below.

If you run the same command again, this time it gives you “SSL certificate add failed. Error 1312” error

In order to resolve this, make sure you have private key along with the certificate, when you install it on DDC server.
- If you have IIS installed on the DDC server, generate csr from that DDC server itself. So, when you import the certificate given by your CA authority, it will link the private key automatically.
- If IIS is not installed on your DDC server, generate CSR from another windows machine and import the certificate given by your CA authority on that server. It will link the private key automatically. Export that certificate along with private key as pfx format and import it in your DDC server.
Now run the above netsh command again. If you still endup in parameter incorrect error, run netsh commands as shown below.
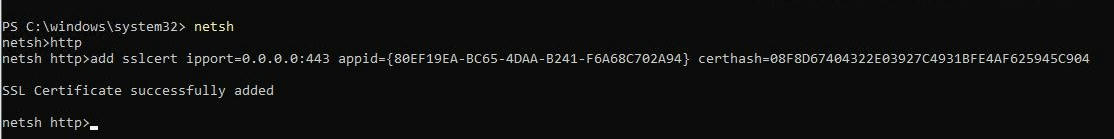
Importing pfx certificate
Use the below commands to import a pfx certificate on server core OS. You cannot import a pfx certificate remotely to a different server.
|
|
Want to learn more on Citrix Automations and solutions???
Subscribe to get our latest content by email.